PowerShell Exploits Analysis
A jsp code was and the code is as above. In simple terms, what the code does is that it will call Powershell, provide true code to be decoded and get executed.
To analyse what the code does, we will display the real code without make sure it runs. To do that,we will paste $(New-Object IO.StreamReader ($(New-Object IO.Compression.DeflateStream ($(New-Object IO.MemoryStream (,$('Encoded String'-split'(..)'|?{$_}|%{[convert]::ToUInt32($_,16)}))),[IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd(); to powershell and execute it.
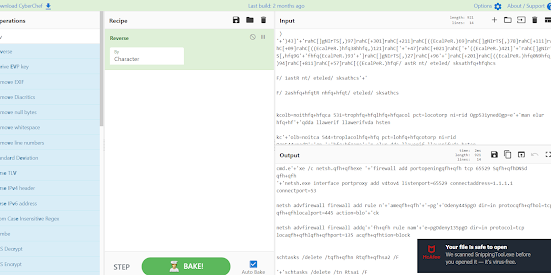
An output like above will be given. The output above is the real payload that powershell will be executing. Before we can analyse it, the output above is in reverse by each character. To undo the reverse, we will paste the code to cyberchef and set reverse by character to undo the reverse.
So are we done here? Not quite yet. Because after a quick analysis on the code, the code was obfuscated so the code need to be reconstructed before a full analysis on the code can be done. In the code, there is a section where some of the characters are replaced with certain random chars.
So we need to reconstruct the code by following the above code. After finish reconstruct the code, then a full analysis on the code can be done.


Comments
Post a Comment